There are a lot of myths and FUD (fear, uncertainty, and doubt) about WordPress security out there. And there’s a lot to consider when hardening a website against potential attacks. So how can businesses learn the WordPress security best practices that will give them the best possible web protection?
Last week, I hosted a webinar conversation to demystify WordPress security concerns. Joining me for the session were Ayush Malakar (full-stack and WordPress developer at Fresh Consulting) and Sean O’Shaughnessy (WordPress VIP Solutions Engineering lead).
Through four guiding questions, these two experts explored security best practices developers, admins, site owners, and executives should keep in mind. Let’s recap what we talked about.
Is open source software secure?
Not all open source is created equal. But as WordPress has been around for 18 years, and powers more than 40% of the world’s websites, it’s clear that adoption is growing. But even with the world’s most popular open source software comes questions about its security vulnerabilities. Isn’t all that code, out in the open, vulnerable to attacks?
Not necessarily, says Ayush: “Since we have so many eyes looking into it, it’s more safe.”
Although it might seem counterintuitive, open source software can actually be more secure than closed source, proprietary software. Here’s why.
More eyes on potential threats
Since open source operates in the open, there is nothing to hide. Many developers in the community are looking at it and making updates, inspiring confidence and trust. If a vulnerability is found, it’s patched as soon as possible—often within a day or two.
Continual code testing and bug bounties
Anyone can contribute to WordPress, and the code is tested by the community of thousands of WordPress core contributors. As the code is continually tested, it’s increasingly reliable.
Additionally, bug bounty programs encourage the public to find holes and vulnerabilities, including brute force attacks, DDoS, phishing, and more.
Security updates
When security updates happen, it’s on website developers to ensure that the core code is kept up to date and protected against the latest attack vectors. Automatic updates are also available, and enterprise developers should consider whether these are the right choice for each project.
“We wanted to use WordPress, and the fact WordPress VIP was the only WordPress option with FedRAMP authorization to operate (ATO) made it a strong option for us as a government agency.”
Kristen Loflin, Public Relations Manager, Marine Corps Marathon Organization
Is my code secure?
WordPress core is just one of the “buckets” of code that make up a WordPress website. Sitting on top of the community-developed software is a website’s application code— its theme or front-end, and plugins.
While the open source WordPress core code is developed by the community, application code written for or deployed to individual websites can also introduce security vulnerabilities.
There are various measures you can take to ensure that your application code is as hardened as possible against attacks. While you might make different decisions for different projects, depending on the level of acceptable risk, the most important thing is to be aware of the potential attack vectors.
Here, our webinar experts have some advice.
Tools for WordPress security
There are various tools that developers can employ to help identify security flaws in both first-party and third-party code.
“Whenever we talk about tools, we need to understand what are the pros and cons of these tools and how we should best use the tools to our advantage?”
— Ayush Malakar, Fresh Consulting
These tools can either perform static or dynamic code analysis. Static analysis is done without executing any of the code, and can usually pick up about 85% of the flaws in the code. Dynamic code analysis relies on studying how the code behaves during execution, and has the additional ability to find security issues caused by the code’s interaction with other system components like SQL databases, application servers, or web services.
It’s important to weigh the benefits of humans vs machines performing this code analysis. Machine learning (ML) and artificial intelligence (AI) can be used as a first line of defence to ensure that common securities are identified. But there’s also value in having a human look at the code afterwards. This ensures that humans can work on different aspects, such as feature-based vulnerability, edge cases, etc.
Some tools our experts recommend:
- WPScan is a CLI tool that developers can use to scan their code for security holes. Ayush recommends developers run this in a cron job.
- PHP_CodeSniffer (PHPCS) inspects code and highlights problems ranging from syntax to security vulnerabilities. There are a set of specific standards for WordPress. This can be set up to run in a Continuous Integration (CI) pipeline, and runs in all WordPress VIP repositories.
- Sonar Cloud, used by Fresh Consulting for static code analysis, scans both PHP and JS code for vulnerabilities and a more secure implementation.
“Are we doing the right amount of input validation? Are we properly sanitizing any sort of output we’re going to have within our code?”
— Sean O’Shaughnessy, WordPress VIP
Security and WordPress plugins
When choosing third-party plugins, look for a plugin that has good reviews and ratings, a high number of downloads, and flexibility to use in your website. Make sure the plugin is updated and is compatible with the latest version of WordPress.
Don’t use a plugin that you can write yourself. Especially in cases where only a small amount of code is needed, write this code in your theme instead of using a plugin. That will ensure that no vulnerabilities will be introduced when updating the plugin.
“What I would recommend is writing the code within the theme itself, because what I’ve seen in the past is plugins that do a very minimal job to make any updates. And chances are, as technology evolves, those plugins do not. The potential of those plugins introducing vulnerabilities might be higher than what we anticipate.”
— Ayush Malakar, Fresh Consulting
As always, it’s important to keep your code updated. Watch out for core and plugin updates, and keep WordPress, plugins, and themes up to date.
It’s WordPress.
Built for business.
Security and WordPress endpoints
XML-RPC and the REST API are endpoints WordPress uses to communicate with other systems, or an application’s front end. It’s important to have an understanding of these endpoints, and whether they will be important to your application, as they are potential attack vectors that can be disabled if not needed.
XML-RPC as a potential attack vector
XML-RPC is a specification that enables communication between WordPress and other systems. In early versions of WordPress, XML-RPC was turned off by default. But since version 3.5, it’s been enabled by default. The main reason for this was to allow the WordPress mobile app to talk to your WordPress installation.
The REST API as a potential attack vector
Ensure using best security practices when using the WordPress REST API. While businesses may need to keep them open, for example in a headless architecture where content needs to flow to a decoupled front end, ensure that those remaining exposed have the proper authentication and authorization.
“You have this castle, WordPress, your application, and having the presence of a drawbridge doesn’t inherently make your application secure. But it is an avenue. It’s a way into that castle. So just having a good understanding and knowing and accounting of those things is definitely vital towards having a better posture around your application security.”
— Sean O’Shaughnessy, WordPress VIP
Is my hosting secure?
There are a lot of considerations to make when determining whether your host is secure enough for your needs. It’s a good idea to consider all the available security options, and don’t forget about the importance of fast support in case of emergencies—like a plugin update causing a security incident.
“Is your hosting provider offering fast and proactive support? Additionally, how are they responding when application or plugin vulnerabilities are published?”
— Sean O’Shaughnessy, WordPress VIP
Overall, look for a platform that considers hosting a shared responsibility. Some features to consider include:
File system permissions
Some hosts offer a read-only file system, rather than being able to write files. This prevents web process users from being able to write files everywhere, closing a potential attack vector.
Containerization
Look for a host that isolates your site’s resources from their other customers’ websites. While this isn’t a comprehensive security measure, containerization does provide a base measure of security. As a bonus, it also allows dedicated resources for horizontal or even vertical scalability.
Version control
When a WordPress hosting platform blocks SFTP and allows for code updates through a version-controlled system, they decrease the attack surface of your application. Additionally, managing application source code through version control provides a “pristine” copy of the code as the source of truth, along with a full, auditable, rich-with-context history of that code.
How can my company enforce WordPress security?
Security is not just a consideration at the code or host level. There are also human factors, and companies can build in processes like regular security checks and password hygiene rules, that will go a long way towards increasing your website’s security.
“At an organizational level, it’s important to think in terms of putting multiple layers of continued authentication or validating in place.”
— Sean O’Shaughnessy, WordPress VIP
Zero trust and least privilege access management
Through carefully considered roles and access management, organizations can equip people to do their job with the least amount of privilege—therefore the least amount of risk—possible. Ensure you properly define and assign the roles and capabilities of users. This capability comes with WordPress out of the box, and can be extended for any use case.
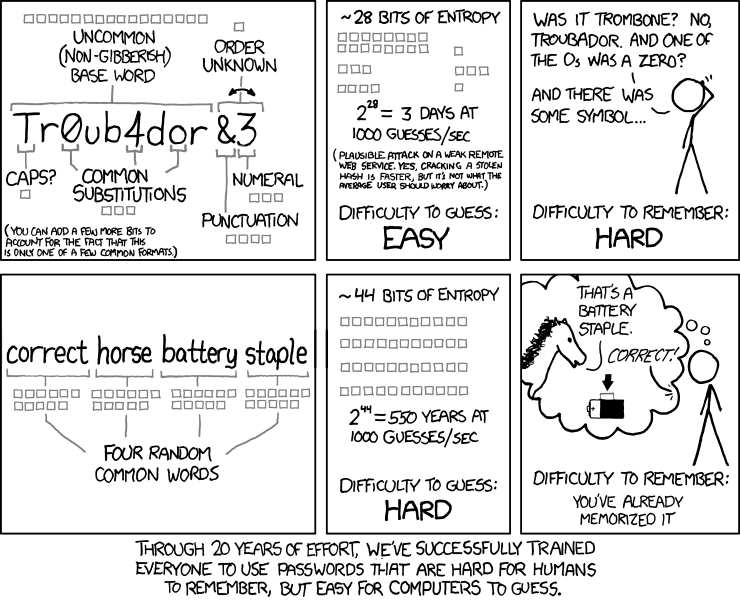
Password hygiene
Users should create unique and hard-to-guess passwords for every application. Sean particularly likes this comic, which advocates for using a collection of random words, rather than a combination of letters, numbers, and symbols:
2FA and SSO
While two-factor authentication (2FA) and single sign-on (SSO) technologies won’t inherently increase the security of your website, they do offer the benefit of centralized user management across all supported applications.
Key WordPress security takeaways
- Open source has security benefits
- Keep WordPress and plugins updated
- Use version control
- Understand the WordPress endpoints
- Look for a host that accounts for security
- Adopt mature security practices on the organization level
We covered a lot more ground about WordPress security in the hour-long webinar. If you missed it live, I encourage you to check out the recording here.



